Malware related to short message services occupies a large portion of today’s Android malware families. These include premium SMS fraud and SMS spying. Such SMS-based malware apps are actively distributed via unofficial or malicious app stores, but it is rare to find them on Google Play, the world’s largest official Android app store. Nonetheless, we have recently seen SMS Trojans on Google Play.
McAfee has found on Google Play two adult-oriented apps in Vietnamese that download a malicious SMS Trojan app impersonating RealPlayer. The malware comes from a remote server and persuades careless users to install and activate it as a DeviceAdmin app.
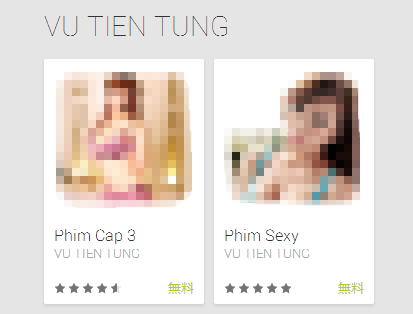
Figure.1: Malicious apps on Google Play that download an SMS Trojan.
These apps look like adult-content viewers, yet at installation they request excessive permissions that are unnecessary for this kind of viewer app.
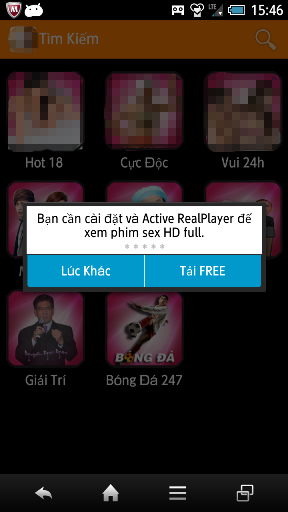
Just after launch, they show a dialog offering to download the latest RealPlayer app for viewing adult movies in HD resolution. The malware downloads RealPlayer.apk if the user accepts.
Figure.2: The dialog to trick users into downloading and installing a fake RealPlayer.
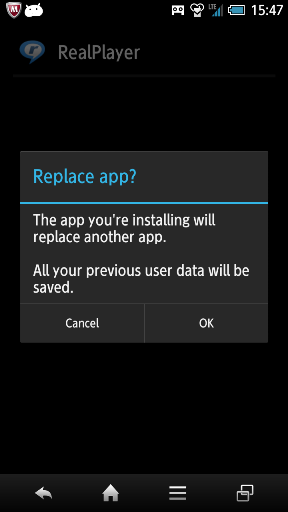
After installation, the user is prompted to accept the first app’s update because the downloaded app also has the same package name as the one that initiated the download.
Figure.3: The confirmation dialog to update the original app with the downloaded one.
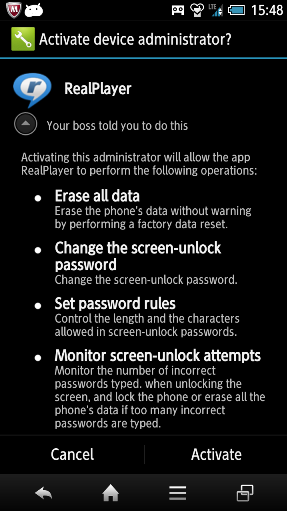
The downloaded app also requests excessive permissions, including SMS-related ones. It requests users to activate it as a DeviceAdmin app. It tries to persuade users by saying “Your boss told you to do this,” although that doesn’t really sound very persuasive. Finally it removes its app icon from home screen to make it invisible to the user.
Figure 4: The confirmation dialog to activate the fake app as a DeviceAdmin.
The downloaded app, which still claims to be RealPlayer, does not allow users to view adult movies in HD. Instead it registers several broadcast receivers triggered by the completion of the device’s boot sequence, adds or removes packages and SMS receipts, and invokes background services that communicates with its control server via HTTP, as seen in typical SMS Trojans on Android.
The app contains the following features:
- Sends SMS messages to a phone number with a text message, both specified in the command from the server.
- Updates the app by downloading the new app package, based on the device’s IMEI and the app package version.
- Discards SMS message received from a predefined set of phone numbers.
- Disables and enables these activities, based on server requests.
The app does nothing special as a DeviceAdmin for now because the current implementation is empty. So it just makes users take extra steps to disable it when uninstalling. However, the Trojan could be updated to a more malicious version at the server’s request.
Installing this malware and others distributed from outside Google Play can be easily blocked if users disable the “installation of apps from unknown sources” option in the device settings. Users need to be very careful about installing apps, especially when they request more permissions than their expected features warrant.
We should be wary of social engineering techniques to drop malware, even the process is initiated by apps on Google Play.
McAfee Mobile Security detects these malicious apps as Android/PhimSms.A and Android/PhimSmsDropper.A.