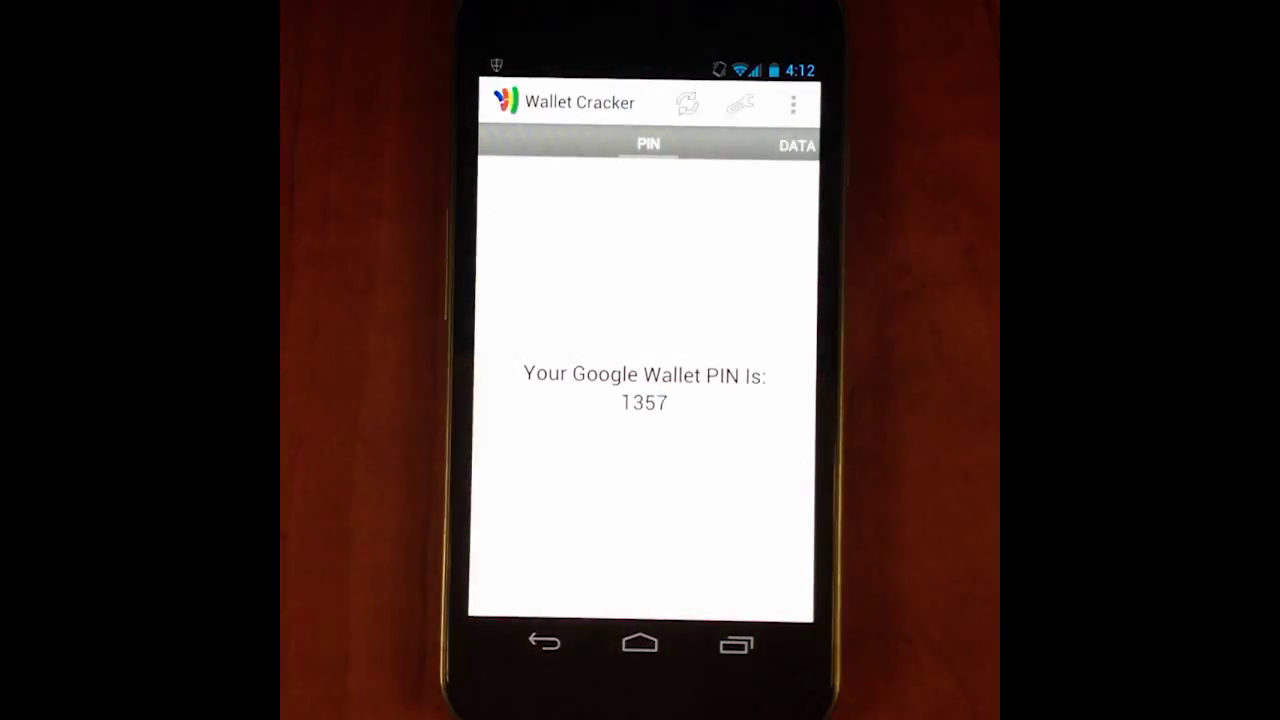
During recent weeks we’ve seen a new botnet kit advertised in several Russian forums. The iDroidbot costs US$1,500 and targets phones running iOS 7.1 and earlier, as well as Android 2.2 and later. The kit has some interesting features, including a credit-card number grabber and a method for draining mobile wallets.
According to the developer, the bot has the following features:
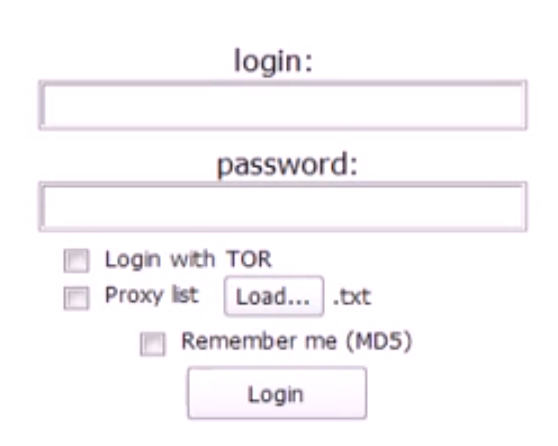
- Web administration
- Windows XP, 7 administration
- Server connection through TOR
- Connection via proxy
The login screen of the panel (in screen above) shows options such as the TOR/Proxy login.
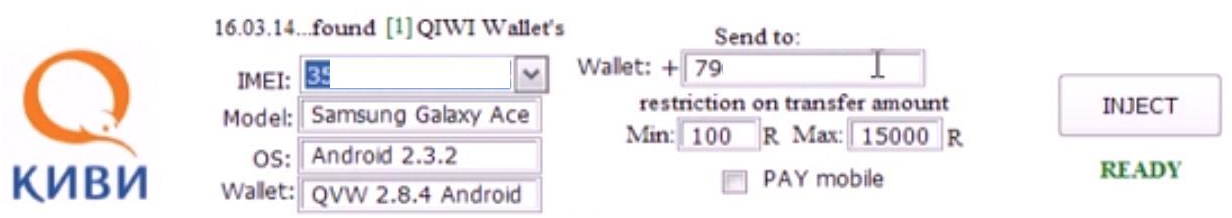
The malware can tap into several mobile wallets:
- Search and inject into purses on infected machines
- Drain a victim’s Visa QIWI Wallet (up to Version 2.8.4) by substituting operations
- Drain WebMoney Keeper Mobile (up to Version 3.0.8 on R and Z purses) by substituting operations
- Drain Yandex 2.2 (up to Version 2.8.4) by substituting operations
The WM/QIWI/Yandex button (below) shows options for stealing from the wallets:
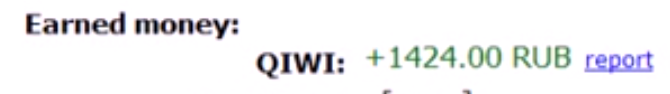
The preceding screenshot demonstrates theft from a QIWI Wallet, whose electronic payment system allows customers to make payments online for items such as utilities, online purchases, and bank loans. In the statistics part of the admin panel, the vendor shows the amount of money earned so far by this setup:
The malware can steal other data, including:
- Keystrokes by tags or by country. The name Troy appears in the processes.
- Credit card numbers by country
- Email by country
Miscellaneous features:
- Sending SMS in stealth mode to a specified number
- Recording conversations in .wav files
- Intercepting SMS from a specific number
- Taking screenshots
According to the seller, the bots can be spread by the following methods:
- Android 2.2 or later—by setting the MIDlet, instructions included
- iOS 7.1 and earlier—by opening the URL and accepting the agreement
- Sewing a MIDlet to any application