This blog post was written by Kumaraguru Velmurugan.
Point of sale (POS) attacks appear to have gained in popularity during the past year or so. We have seen major retail chains targeted by different strains of POS malware. Equipped with memory-scraping functionality, POS malware steals credit or debit card information from shoppers who use their cards for payments.
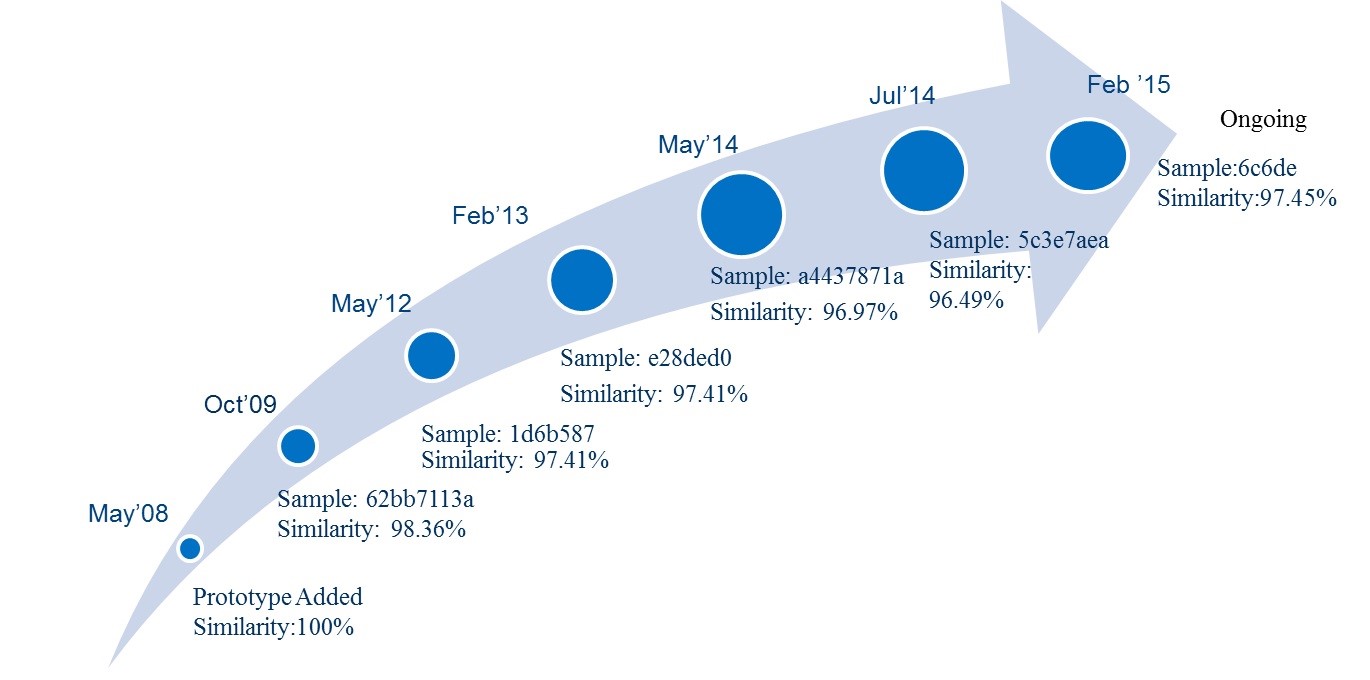
The following illustration shows the similarity of a recent variant we have captured against previous samples we’ve seen. The code has undergone minimal changes since its inception.
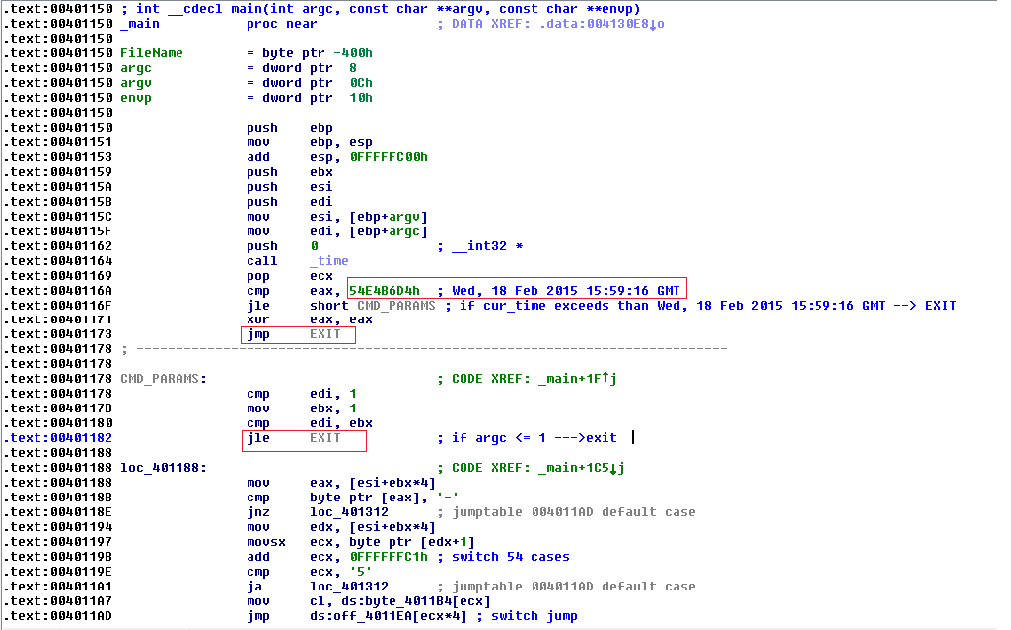
Black POS malware is one of the most prevalent POS families in the wild. Recently we noticed new variants of Black POS that exhibit no behavior when executed in a synthetic environment. This inactivity in a sandbox promptly captured our attention. This new variant of Black POS checks the system time on the infected machine against the hardcoded time stamp on the executable. (Malware has long used this technique to be active only during certain periods, while remaining dormant the rest of the time.)
This variant of Black POS was compiled with Borland C++. Next we see one sample’s main function, in which time is checked against a preset value.
Looking at the malware’s time stamp, Wed 14 Jan 2015 18:14:29 GMT, we see the malware is designed to exhibit its behavior for one month from the time it was compiled.
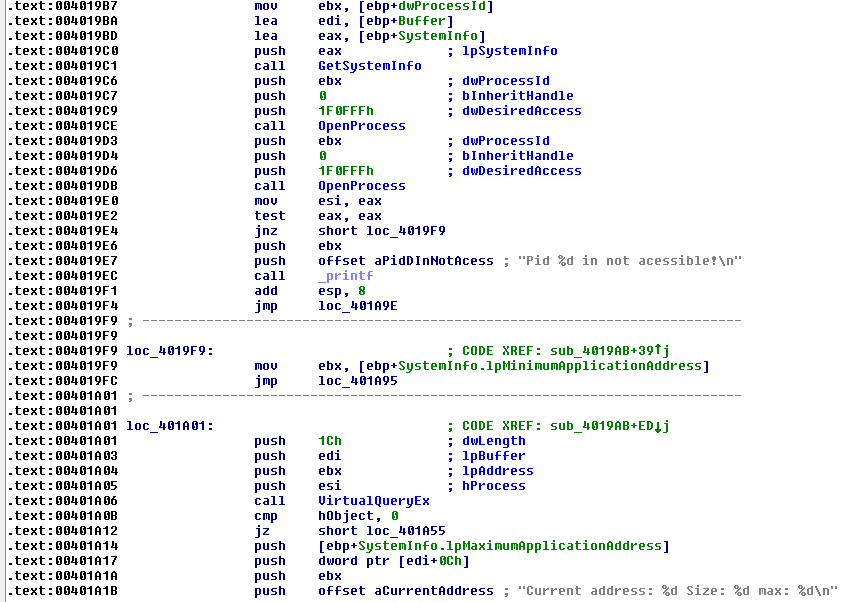
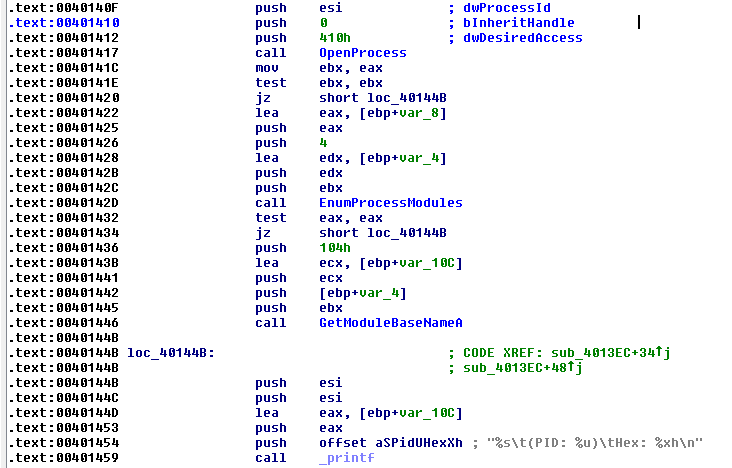
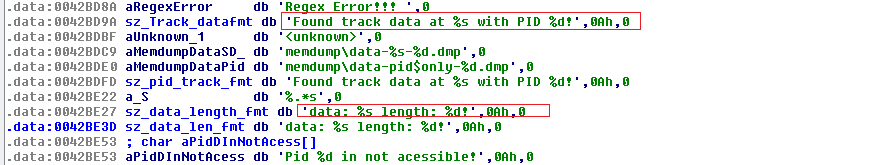
The key functions of this sample include memory dumping and enumerating modules loaded in process memory.
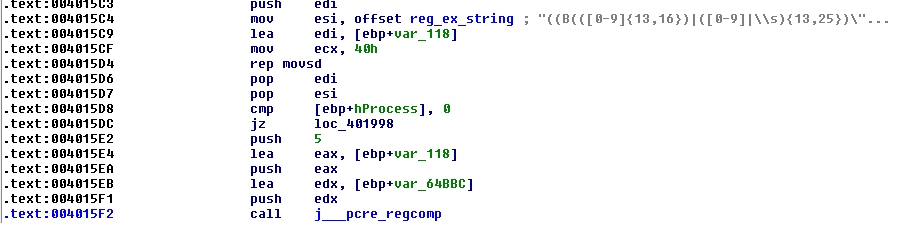
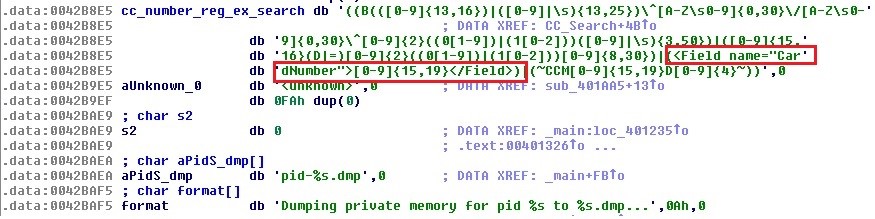
The sample also scans for credit card information in memory by employing a Perl Compatible Regular Expressions engine, as shown in the following image.
McAfee Advanced Threat Defense
McAfee Advanced Threat Defense detects the samples involved in this attack. The sample is detected via static code analysis, the Family Classification module.