If you are unsure of whether a destination link is safe, tools like TrustedSource are a good place to start.
A recently released McAfee report titled “Hacking into the Human Operating System”
- Investigates the role of social engineering within cybersecurity
- Dives into the lifecycle of a social engineering attack (Research, Hook, Play, Exit)
- Analyzes influencing psychological levers that yield the most success to engage the target for a successful attack execution.
If you’ve been following the news lately, the relentless string of major data breaches impacting millions of customers has affected every major business sector. What remains frightening is how a wave of phishing soars in the aftermath of any major breach, putting those that were impacted by the breach at possibly more risk, and putting those that were not impacted by the breach still in the crosshairs.
Social engineering almost always has a place in the success of these attacks; bringing to light the psychological levers these adversaries rely on to execute successful attacks can help disrupt these events from occurring. Of the six influencing psychological levers mentioned in “Hacking the Human Operating System,” scarcity is an influencing lever used as a mainstay of email phishing attacks, so I wanted to dive a bit deeper into this one.
Scarcity boils down to a limited window of time that’s available to act. It can stretch to both ends of the spectrum – act now to gain something, or act now or else lose something. By doing so, it appeals to targets who are motivated by the opportunity for gain, and conversely preys on targets fearing the risk of loss by inaction.
Examples of missed opportunity:
- “I came across your profile and couldn’t help but get excited. We have a really great opportunity for you at our company.”
- “For a limited time…”
Examples of fear of inaction:
- “Failure to respond within 24 hours will result in restricted access to your account.”
- “Click to upgrade your email by Friday for uninterrupted access.”
- ”To ensure your privacy, log in within the next 48 hours to validate your settings.”
- “Your email account has exceeded its limit, and you may not be able to send or receive messages. Click here to upgrade your account.”
Particularly, when lures are information-rich and target-relevant, a victim’s impetus to act is extremely strong. Let’s take a look at an example of an attack that uses the scarcity of time to prey on the victim. I’ve numerically annotated sections of the email below to help facilitate the analysis.
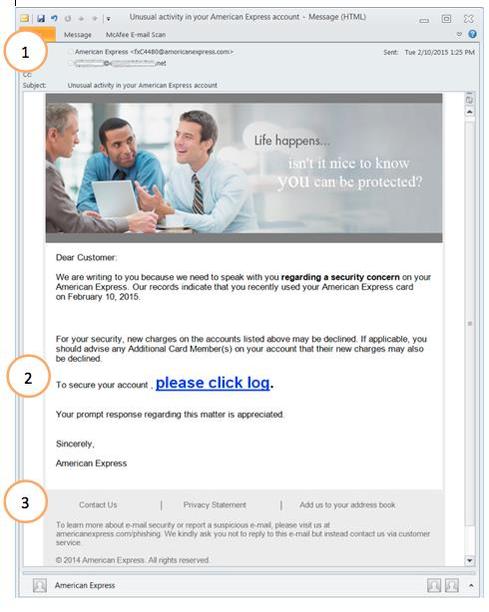
At first glance, a few things look correct when looking into the details:
1. The email sender appears to be from “American Express.”
3. Hovering over the “Contact Us,” “Privacy Statement,” and “Add us to your address book” appears to lead to the legitimate American Express site. All domains here begin with https://americanexpress.com.
Upon closer look, there are clues that reveal otherwise:
- While the email sender and sender address were fully displayed when I viewed the email on my desktop mail client, it wasn’t as obvious from my mobile device (see below). Upon further inspection, the sender email is fxC4480@amoricanexpress.com. The misspelling in the domain name, amoricanexpress instead of americanexpress, should trigger suspicion. It’s always worthwhile to take a closer look at the sender address.

- Hover over any links before you click on them. On my iPhone, holding down the “please click log” call to action link reveals it leads to http://xx.xxx.xxx.xxx/americanexpress. (IP address has been obfuscated as it leads to a malicious site.) The fact that an IP address was used in lieu of a domain name might be reason to raise suspicion, especially given that the links in item 3 use the proper domain name (www.americanexpress.com). Further, the inconsistency in using both IPs and domains on the same page may also raise a red flag.
If you are unsure of whether a destination link is safe, tools likeTrustedSource are a good place to start. You can leverage this type of resource to help you check the reputation of a Web page simply by querying its IP address, domain name, or URL. Keep in mind ultra-low prevalence targeted attacks may originate from a new server that lacks reliable reputation information, so while TrustedSource.org is a good place to start, it may not catch all poor reputations.
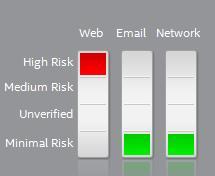
In this particular case, rather than click on the link, which may land me on a malicious site, I can go to TrustedSource.org and enter the IP address hiding behind the “please click log.” The results reveal that this IP address carries a high risk and is likely not safe (see chart below).
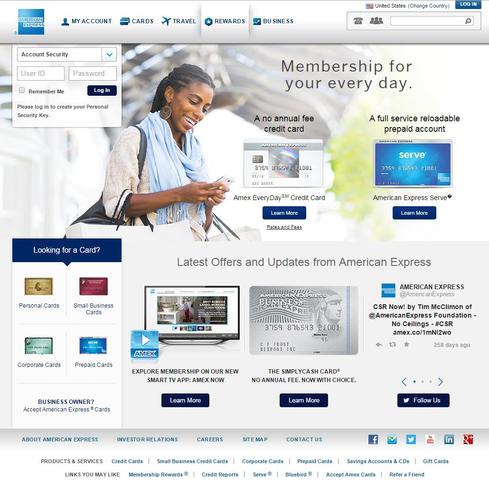
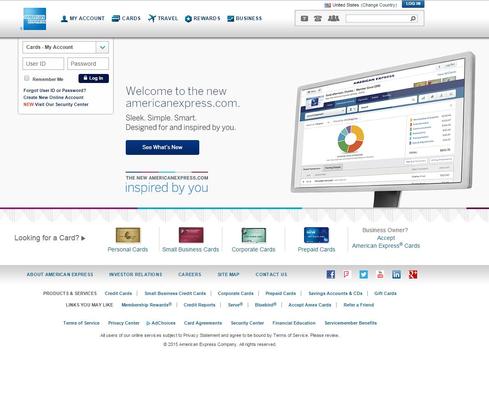
And indeed, the link leads to a spoofed phishing site. At a glance, can you tell which is the legitimate site and which is a spoofed phishing site? (Answer will be revealed at the end.)
To learn more about the psychology and nature of social engineering attacks, a full copy of the research report “Hacking the Human Operating System” can be found here. You can also run an awareness program within your organization using the quiz to better understand your risk profile.
And by the way, the first of the two images above is from the spoofed site, and the second is from the legitimate site. How did you fare?
View the original post on Dark Reading.
Resources:
American Express’s resources on steps to safeguard yourself:
https://www.americanexpress.com/us/content/fraud-protection-center/home.html











