Adobe Flash Player has been a boon to Android malware creators for a long time. These developers have taken advantage of Flash’s popularity to create premium SMS Trojans and droppers, as well as other types of malware. McAfee Labs has detected a common scam app–Android/Fladstep.B–on the Google Play store since the end of 2013. The malware tricks users into paying money via PayPal to install Flash Player. The malware is removed from the store every time it appears, but we have found that the same attacks are again on Google Play.
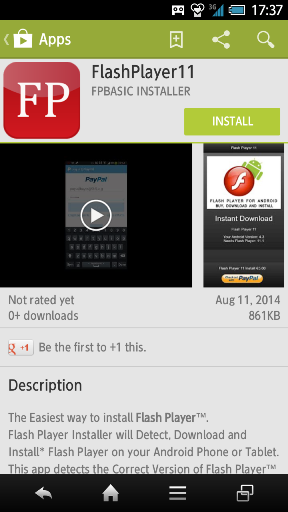
Examples of Flash Player installer scam apps on Google Play store.
Multiple apps claiming to be installers of Flash Player have been published by several app developer accounts since the end of June. The malware is short lived, but the total download count of those apps amounts to more than 50,000, according to Google Play statistics. These apps were quickly removed, but they reappear soon with different names and developer accounts.
A Flash Player installer scam app that has been just published.
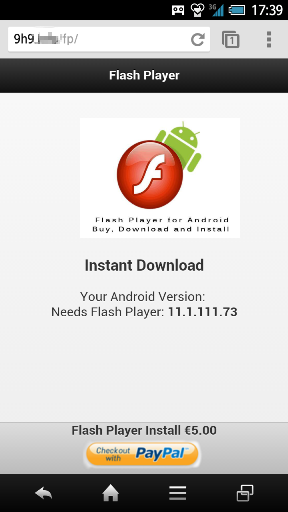
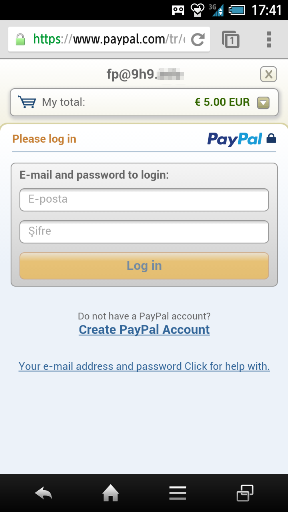
When launched, this scam app simply opens a web page that requests users to pay a €5 fee via PayPal to install Flash Player. The web page is hosted on a server located in Turkey in some apps and the United States in other apps. If the user pays the fee with the PayPal account, the web page shows a download link to Flash Player that is the legitimate URL of Adobe’s download site.
The malicious web page requesting users to pay with PayPal for Flash Player installation.
PayPal payment screen.
In short, victims are tricked into paying money for a free download. The scammer might claim that the installer app provides an “added value” to automatically detect the version of the Flash Player appropriate to the user’s Android OS version, but this version identification is easy to do by checking Adobe’s download site.
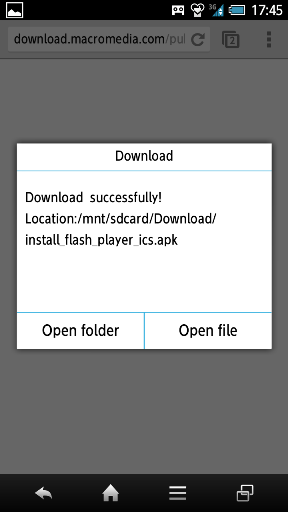
The download link shown after payment points to the real Adobe download site.
The Flash Player downloaded from the Adobe’s site.
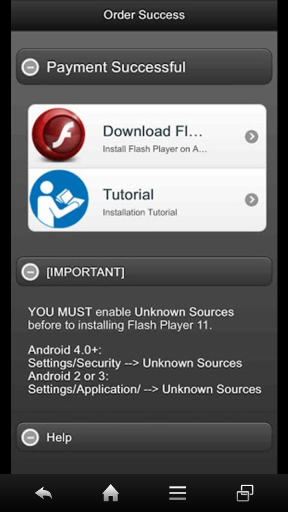
Another sin of this scam app is that the app’s description page on Google Play shows some screen images including one that implies the user can get both Flash Player and its “tutorial.” However, no tutorial is supplied, even to users who pay; they get exactly the same package as everyone else.
The screen shot on Google Play that promises a tutorial.
Last, paying with PayPal gives the user’s name and email address to the app developer, who can easily collect and abuse the personal information of these victims. Those who are careless enough to be scammed even once can easily be targeted in future scams.
Flash Player will continue to benefit malware authors due to its popularity. And this type of scam will continue because criminals can easily and directly get money from their victims using popular online payment services. Users should be very careful about the sellers of products when using online payments, for example, by checking that the name and contact information of the company or seller is explicitly displayed and that the product is really what they want to buy.
Fight Back With McAfee
McAfee Mobile Security detects these Android scam apps as variants of Android/Fladstep, and also blocks browser access to websites hosting this scam.