Over the weekend Google released the Android Market Security Tool to help clean up devices infected with the DroidDream malware. The Android/DrdDream family of malware used a pair of exploits (Expoit/LVedu and Exploit/DiutesEx) to gain root access on vulnerable Android devices. More than 50 Android applications were reported to be infected; all were pulled from the Android Market. The applications were all versions of legitimate programs that were repackaged by the malware authors with malicious code.
Android/DrdDream sends a collection of information (IMEI, IMSI, OS version, etc.) to the attacker and also attempts to download additional payloads. Although the malware uses the pair of root exploits, it doesn’t actually need root access to send the data to the attacker.
Inside the Android Market Security Tool
Google has its official statement on the the tool on the Android Market help site. They list a number of steps they’ve taken to remedy Android/DrdDream (“March 2011 Security Issue”):
- Suspending the developer accounts (three users) and removing the malicious applications from Android Market
- Remotely uninstalling the malicious apps from infected devices
- Pushing out the Android Market Security Tool to infected devices
Disabling accounts, taking apps out of the store, and hitting the remote-app kill switch were already well known ways for handling bad Android apps. Sending a security application to a phone is a whole new addition to the toolbox.
As a security researcher I find it interesting to see how new security tools are put together, more so when they come from an operating system developer. Normally I dig into the internals of malware; this time I got to see inside a mobile malware removal tool. Google’s security tool is available on the Android Market, so I was able to grab a copy for analysis.
The Android Market Security Tool is an Android app that also has a non-Dalvik native application component called droidreamclean. Android/DrdDream drops a few additional files (native binaries, an additional APK, etc.) on an infected phone. Because the files are located outside of the app directory, simply uninstalling the app won’t remove them from the phone. Really cleaning the phone requires access to the file system at a level that standard Android applications can’t reach. The security app launches droiddreamclean to delete the additional files and restore some security settings.
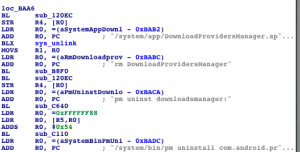
After it gains root access, Android/DrdDream attempts to copy a second payload from its assets directory to the application directory (/system/apps/DownloadProviderManager.apk). This is a manual installation that completely bypasses the Android Market and because the Market doesn’t record the installation, it can’t be remotely killed. droiddreamclean doesn’t have this problem and instead tries a couple of uninstallation methods: using the “pm” package manager or manually deleting the APK.
The malware copies a renamed “su” executable (/system/bin/profile) to a directory of other system commands. This allows the attacker or updated malware to gain root access in the future. The Security Tool gives that executable the same treatment as the downloader component of Android/DrdDream.
In case the remote kill does not work, the security tool includes a list of apps that are removed using the command-line package manager. The Android/DrdDream authors definitely are not going to be able to slip one through.

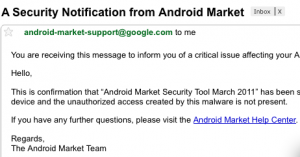
After droiddreamclean finishes, the Android Market Security Tool informs Google that your phone is now clean. It then uninstalls itself. At the end of all this, you get an email from Google telling you that it has removed the malware and that no issues remain.
Is the Android Market Security Tool enough?
The Android Market Security Tool is a pretty comprehensive tool, but it’s really designed only to clean up Android/DrdDream and its side effects. The tool itself doesn’t patch or reflash the operating system, so the vulnerabilities exploited by Android/DrdDream will remain. Updating the operating system will require help from the manufacturers of the various affected Android devices.
For similar infections, Google might have to follow the route that other security software takes and provide regular updates. The creation of the security tool and the work put into handling the Android/DrdDream issue shows that Google understands the need for mobile security software.











