Last Thursday morning (October 31), our Advanced Exploit Detection System (AEDS), which we discussed in an earlier post, detected a suspicious sample targeting Microsoft Office. After some investigation, we confirmed this is a zero-day attack.
Our Findings
Considering the importance of this incident, we shared our findings immediately with the Microsoft Security Response Center and worked closely with them in the last couple days. Today, as Microsoft has publicly released the security advisory with mitigations and workarounds, we feel it is time to share some detail of this zero-day attack.
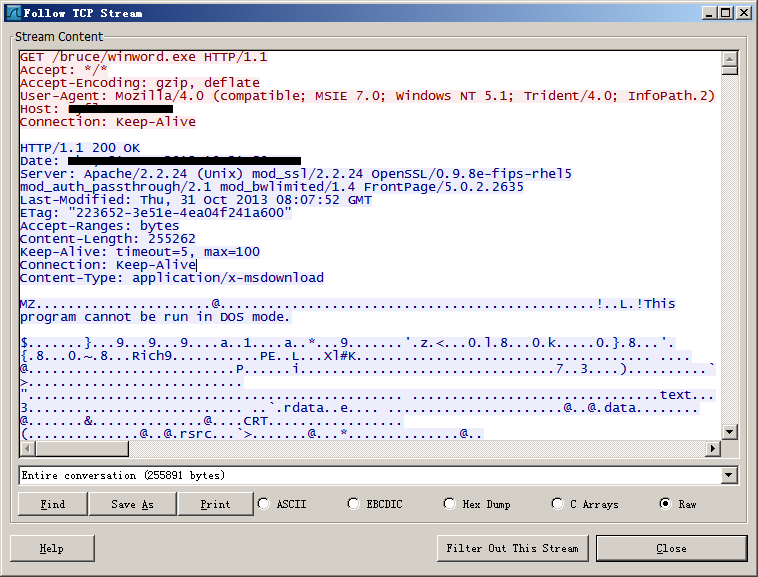
Here is the traffic captured by this attack on a fully updated version of Office 2007 running on Windows XP SP3.
As we can see, after successful exploitation, the exploit downloads an executable (saved to C:\Documents and Settings\<username>\Local Settings\Temp\winword.exe) from the controlled web server.
The executable is actually a RAR SFX containing another executable and a fake Word document. The another executable (dropped to C:\Documents and Settings\<username>\Updates.exe) is a backdoor allowing attacker to take control of the victim’s computer. The fake document (dropped to C:\Documents and Settings\<username>\Shanti.doc) is popped to the victim right after the success of the exploitation, this is a common post-exploitation trick which tries to prevent victims from being aware of this attack.
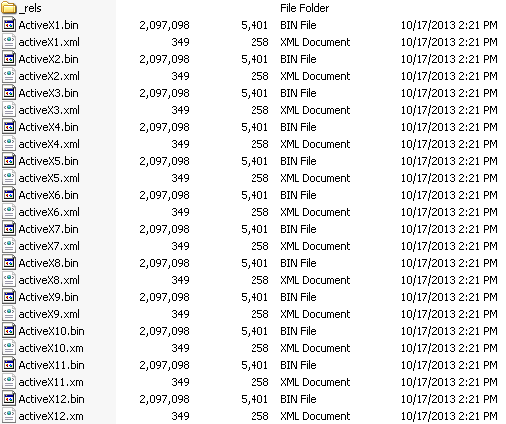
The zero-day exploit sample is organized as the Word OpenXML format (.docx). We observed many ActiveX objects contained in the “activeX” directory after unzipping the .docx file. This suggests that the exploit uses ActiveX control to spray the heap memory.
It is worth to note that this heap-spraying in Office via ActiveX objects is a new exploitation trick which we didn’t see before, previously attackers usually chose Flash Player to spray memory in Office. We would believe the new trick was developed under the background that Adobe introduced a click-to-play feature in Flash Player months ago, which basically killed the old one. This is another proof that attacking technique always tries to evolve when old ones don’t work anymore.
As it shows, the meta date of the files were set to October 17, 2013, which may suggest a creation time of this exploit (though, the meta time could be faked).
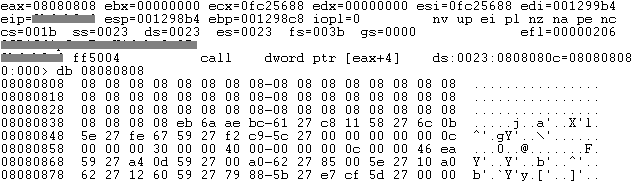
And this is the place that EIP is being controlled to a sprayed memory space 0x08080808.
Speaking on the vulnerability leveraged by this attack, while we spotted the attack performed via Office 2007 running on Windows XP, this is actually a fault existing in a TIFF-processing component shipped with Microsoft Office. Therefore, not only are Office 2007 with Windows XP vulnerable to this attack, but also more environments are affected by this vulnerability. In addition, our later research showed this exploit also works on Office 2007 running on Windows 7. We’d suggest that readers take a look at the SRD blog post where they shared the exact affected environments and views from the vendor’s perspective. The Labs has been actively working on getting every piece of details of this exploit, we may share our additional findings in the near future.
Our AEDS continues to monitor advanced threats such as zero-day exploits and APTs worldwide, as a part of our commitments to protect our customers from today’s fast-evolving attacks.
For McAfee customers, we have released NIPS signature “UDS-ShantiMalwareDetected” last Friday to deliver protection in advance, our HIPS product is able to detect this attack without any update.
Thanks Bing Sun, Chong Xu, Xiaoning Li (McAfee Labs) and Lijun Cheng for their hard work on the exploit analysis as well as IPS detections. Guilherme Venere and Abhishek Karnik also contributed from the anti-virus side.